by Blog | May 20, 2024 | Cybersecurity
With cyber threats evolving at an alarming pace, staying ahead of the curve is crucial. It’s a must for safeguarding sensitive information. Data security threats are becoming more sophisticated and prevalent. The landscape must change to keep up. In 2024, we can expect exciting developments alongside persistent challenges.
Over 70% of business professionals say their data privacy efforts are worth it. And that their business receives “significant” or “very significant” benefits from those efforts.
Staying informed about these trends is crucial. This is true whether you’re an individual or a business safeguarding valuable data.
Here are some key areas to watch.
1. The Rise of the Machines: AI and Machine Learning in Security
Artificial intelligence (AI) and machine learning (ML) are no longer futuristic concepts. They are actively shaping the cybersecurity landscape. This year, we’ll likely see a further rise in their application:
- Enhanced Threat Detection: AI and ML algorithms excel at analyzing massive datasets. This enables them to identify patterns and anomalies that might escape human notice. This translates to a quicker detection of and reaction to potential cyber threats.
- Predictive Analytics: AI can predict potential vulnerabilities and suggest proactive measures. It does this by analyzing past cyberattacks and security incidents.
- Automated Response: AI can go beyond detection and analysis. Professionals can program it to automatically isolate compromised systems. As well as block malicious activity and trigger incident response procedures. This saves valuable time and reduces the potential impact of attacks.
AI and ML offer significant benefits. But it’s important to remember they are tools, not magic solutions. Deploying them effectively requires skilled professionals. Experts who can interpret the data and make informed decisions.
2. Battling the Ever-Evolving Threat: Ransomware
Ransomware is malicious software that encrypts data and demands a ransom for decryption. It has been a persistent threat for years. Unfortunately, it’s not going anywhere in 2024. Hackers are constantly refining their tactics, targeting individuals and businesses alike. Here’s what to expect:
- More Targeted Attacks: Hackers will likely focus on meticulously selecting high-value targets. Such as critical infrastructure or businesses with sensitive data. They do this to maximize their impact and potential payout.
- Ransomware-as-a-Service (RaaS): This enables those with limited technical expertise to rent ransomware tools. This makes it easier for a wider range of actors to launch attacks.
- Double Extortion: Besides encrypting data, attackers might steal it beforehand. They then may threaten to leak it publicly if the ransom isn’t paid, adding pressure on victims.
3. Shifting Strategies: Earlier Data Governance and Security Action
Traditionally, companies have deployed data security measures later in the data lifecycle. For example, after data has been stored or analyzed. But a new approach towards earlier action is gaining traction in 2024. This means:
- Embedding Security Early On: Organizations are no longer waiting until the end. Instead, they will integrate data controls and measures at the start of the data journey. This could involve setting data classification levels. As well as putting in place access restrictions. They will also be defining data retention policies early in the process.
- Cloud-Centric Security: More organizations are moving towards cloud storage and processing. As they do this, security solutions will be closely integrated with cloud platforms. This ensures consistent security throughout the entire data lifecycle.
- Compliance Focus: Data privacy regulations like GDPR and CCPA are becoming increasingly stringent. As this happens, companies will need to focus on data governance to ensure compliance.
4. Building a Fortress: Zero Trust Security and Multi-Factor Authentication
We’re in a world where traditional perimeter defenses are constantly breached. This is why the “Zero Trust” approach is gaining prominence. This security model assumes that no user or device is inherently trustworthy. Users and programs need access verification for every interaction. Here’s how it works:
- Continuous Verification: Every access request will be rigorously scrutinized. This is regardless of its origin (inside or outside the network). Systems base verification on factors like user identity, device, location, and requested resources.
- Least Privilege Access: Companies grant users the lowest access level needed to perform their tasks. This minimizes the potential damage if hackers compromise their credentials
- Multi-Factor Authentication (MFA): MFA adds an important extra layer of security. It requires users to provide extra factors beyond their password.
5. When Things Get Personal: Biometric Data Protection
Biometrics include facial recognition, fingerprints, and voice patterns. They are becoming an increasingly popular form of authentication. But this also raises concerns about the potential for misuse and privacy violations:
- Secure Storage Is Key: Companies need to store and secure biometric data. This is ideally in encrypted form to prevent unauthorized access or breaches.
- Strict Regulation: Expect governments to install stricter regulations. These will be around the collection, use, and retention of biometric data. Organizations will need to ensure they adhere to evolving standards. They should also focus on transparency and user consent.
How to Prepare for Evolving Data Security Trends
Feeling a bit overwhelmed? Don’t worry, here are some practical steps you and your organization can take:
- Stay Informed
- Invest in Training
- Review Security Policies
- Embrace Security Technologies
- Test Your Systems
Schedule a Data Security Assessment Today!
The data security landscape of 2024 promises to be both intriguing and challenging. We can help you navigate this evolving terrain with confidence.
A data security assessment is a great place to start. Contact us today to schedule yours.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
by Blog | May 15, 2024 | Cybersecurity
Have you been hearing more about email authentication lately? There is a reason for that. It’s the prevalence of phishing as a major security threat. Phishing continues as the main cause of data breaches and security incidents. This has been the case for many years.
A major shift in the email landscape is happening. The reason is to combat phishing scams. Email authentication is becoming a requirement for email service providers. It’s crucial to your online presence and communication to pay attention to this shift.
Google and Yahoo are two of the world’s largest email providers. They have implemented a new DMARC policy that took effect in February 2024. This policy essentially makes email authentication essential. It’s targeted at businesses sending emails through Gmail and Yahoo Mail.
But what’s DMARC, and why is it suddenly so important? Don’t worry, we’ve got you covered. Let’s dive into the world of email authentication. We’ll help you understand why it’s more critical than ever for your business.
The Email Spoofing Problem
Imagine receiving an email seemingly from your bank. It requests urgent action. You click a link, enter your details, and boom – your information is compromised.
The common name for this is email spoofing. It’s where scammers disguise their email addresses. They try to appear as legitimate individuals or organizations. Scammers spoof a business’s email address. Then they email customers and vendors pretending to be that business.
These deceptive tactics can have devastating consequences on companies. These include:
- Financial losses
- Reputational damage
- Data breaches
- Loss of future business
Unfortunately, email spoofing is a growing problem. It makes email authentication a critical defense measure.
What is Email Authentication?
Email authentication is a way of verifying that your email is legitimate. This includes verifying the server sending the email. It also includes reporting back unauthorized uses of a company domain.
Email authentication uses three key protocols, and each has a specific job:
- SPF (Sender Policy Framework): Records the IP addresses authorized to send email for a domain.
- DKIM (DomainKeys Identified Mail): Allows domain owners to digitally “sign” emails, verifying legitimacy.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): Gives instructions to a receiving email server. Including, what to do with the results of an SPF and DKIM check. It also alerts domain owners that their domain is being spoofed.
SPF and DKIM are protective steps. DMARC provides information critical to security enforcement. It helps keep scammers from using your domain name in spoofing attempts.
Here’s how it works:
- You set up a DMARC record in your domain server settings. This record informs email receivers (like Google and Yahoo). It tells them the IP addresses authorized to send emails on your behalf.
- What happens next? Your sent email arrives at the receiver’s mail server. It is looking to see if the email is from an authorized sender.
- Based on your DMARC policy, the receiver can take action. This includes delivery, rejection, or quarantine.
- You get reporting back from the DMARC authentication. The reports let you know if your business email is being delivered. It also tells you if scammers are spoofing your domain.
Why Google & Yahoo’s New DMARC Policy Matters
Both Google and Yahoo have offered some level of spam filtering. But didn’t strictly enforce DMARC policies. The new DMARC policy raises the bar on email security.
- Starting in February 2024, the new rule took place. Businesses sending over 5,000 emails daily must have DMARC implemented.
- Both companies also have policies for those sending fewer emails. These relate to SPF and DKIM authentication.
Look for email authentication requirements to continue. You need to pay attention to ensure the smooth delivery of your business email.
The Benefits of Implementing DMARC:
Implementing DMARC isn’t just about complying with new policies. It offers a range of benefits for your business:
- Protects your brand reputation: DMARC helps prevent email spoofing scams. These scams could damage your brand image and customer trust.
- Improves email deliverability: Proper authentication ensures delivery. Your legitimate emails reach recipients’ inboxes instead of spam folders.
- Provides valuable insights: DMARC reports offer detailed information. They give visibility into how different receivers are handling your emails. As well as help you identify potential issues. They also improve your email security posture.
Taking Action: How to Put DMARC in Place
Implementing DMARC is crucial now. This is especially true considering the rising email security concerns with email spoofing. Here’s how to get started:
- Understand your DMARC options
- Consult your IT team or IT security provider
- Track and adjust regularly
Need Help with Email Authentication & DMARC Monitoring?
DMARC is just one piece of the email security puzzle. It’s important to put email authentication in place. This is one of many security measures required in the modern digital environment. Need help putting these protocols in place? Just let us know.
Contact us today to schedule a chat.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
by Blog | May 10, 2024 | Cybersecurity
Have you ever seen a video of your favorite celebrity saying something outrageous? Then later, you find out it was completely fabricated? Or perhaps you’ve received an urgent email seemingly from your boss. But something felt off.
Welcome to the world of deepfakes. This is a rapidly evolving technology that uses artificial intelligence (AI). It does this to create synthetic media, often in the form of videos or audio recordings. They can appear real but are actually manipulated.
People can use deepfakes for creative purposes. Such as satire or entertainment. But their potential for misuse is concerning. Deepfakes have already made it into political campaigns. In 2024, a fake robocall mimicked the voice of a candidate. Scammers wanted to fool people into believing they said something they never said.
Bad actors can use deepfakes to spread misinformation. As well as damage reputations and even manipulate financial markets. They are also used in phishing attacks. Knowing how to identify different types of deepfakes is crucial in today’s world.
So, what are the different types of deepfakes, and how can you spot them?
Face-Swapping Deepfakes
This is the most common type. Here the face of one person is seamlessly superimposed onto another’s body in a video. These can be quite convincing, especially with high-quality footage and sophisticated AI algorithms.
Here’s how to spot them:
- Look for inconsistencies: Pay close attention to lighting, skin tones, and facial expressions. Do they appear natural and consistent throughout the video? Look for subtle glitches. Such as hair not moving realistically. Or slight misalignments around the face and neck.
- Check the source: Where did you encounter the video? Was it on a reputable news site or a random social media page? Be cautious of unverified sources and unknown channels.
- Listen closely: Does the voice sound natural? Does it match the person’s typical speech patterns? Incongruences in voice tone, pitch, or accent can be giveaways.
Deepfake Audio
This type involves generating synthetic voice recordings. They mimic a specific person’s speech patterns and intonations. Scammers can use these to create fake audio messages. As well as make it seem like someone said something they didn’t.
Here’s how to spot them:
- Focus on the audio quality: Deepfake audio can sound slightly robotic or unnatural. This is especially true when compared to genuine recordings of the same person. Pay attention to unusual pauses. As well as inconsistent pronunciation or a strange emphasis.
- Compare the content: Does the content of the audio message align with what the person would say? Or within the context in which it’s presented? Consider if the content seems out of character or contradicts known facts.
- Seek verification: Is there any independent evidence to support the claims made? If not, approach it with healthy skepticism.
Text-Based Deepfakes
This is an emerging type of deepfake. It uses AI to generate written content. Such as social media posts, articles, or emails. They mimic the writing style of a specific person or publication. These can be particularly dangerous. Scammers can use these to spread misinformation or impersonate someone online.
Here’s how to spot them:
- Read critically: Pay attention to the writing style, vocabulary, and tone. Does it match the way the person or publication typically writes? Look for unusual phrasing, grammatical errors, or inconsistencies in tone.
- Check factual accuracy: Verify the information presented in the text against reliable sources. Don’t rely solely on the content itself for confirmation.
- Be wary of emotional triggers: Be cautious of content that evokes strong emotions. Such as fear, anger, or outrage. Scammers may be using these to manipulate your judgment.
Deepfake Videos with Object Manipulation
This type goes beyond faces and voices. It uses AI to manipulate objects within real video footage. Such as changing their appearance or behavior. Bad actors may be using this to fabricate events or alter visual evidence.
Here’s how to spot them:
- Observe physics and movement: Pay attention to how objects move in the video. Does their motion appear natural and consistent with the laws of physics? Look for unnatural movement patterns. As well as sudden changes in object size, or inconsistencies in lighting and shadows.
- Seek original footage: If possible, try to find the original source of the video footage. This can help you compare it to the manipulated version and identify alterations.
Staying vigilant and applying critical thinking are crucial in the age of deepfakes.
Familiarize yourself with the different types. Learn to recognize potential red flags. Verify information through reliable sources. These actions will help you become more informed and secure.
Get a Device Security Checkup
Criminals are using deepfakes for phishing. Just by clicking on one, you may have downloaded a virus. A device security checkup can give you peace of mind. We’ll take a look for any potential threats and remove them.
Contact us today to learn more.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
by Blog | May 5, 2024 | Cybersecurity
Back when you were a kid, living in a “smart home” probably sounded futuristic. Something out of Back to the Future II or The Jetsons. Well, we don’t yet have flying cars, but we do have video telephones as well as smart refrigerators and voice-activated lights.
But even the most advanced technology can have analog problems. Hackers can get past weak passwords. Bad connections can turn advanced into basic pretty quickly.
Have you run into any issues with your smart home gadgets? Not to worry! We’ve got your back when it comes to troubleshooting several common smart home issues.
Here are some of the most frequent problems along with simple steps to get your smart haven back on track.
1. Connectivity Woes
Are your smart gadgets refusing to connect to Wi-Fi? The main claim to fame of smart devices is that you can access them wirelessly. An internet connection is also vital to integrate several devices into a smart home hub.
If your device is having connection issues, check the basics first. Restart your router and your devices. If that doesn’t work, ensure you’ve positioned your router centrally. This gives you optimal signal strength. Consider a mesh network for large houses. Or invest in a Wi-Fi extender for better coverage.
2. Device Unresponsiveness
Now that we have voice-activated devices, we expect them to always answer. It can be frustrating when a device won’t respond to its “wake word.” We might even raise our voice and ask again… only to be ignored.
Are you having trouble with your smart devices not responding to commands? A simple power cycle (turning them off and on) can often do the trick. Check for software updates on your devices. As well as the corresponding apps. Updating software can fix bugs and improve performance.
3. Battery Drain
Smart devices, especially those battery-powered, can drain quickly. Adjust settings to reduce power consumption. Disable features you don’t use. Such as notification lights or constant background updates. Consider replacing batteries with high-quality ones for optimal performance.
4. Incompatibility Issues
Not all smart devices are created equal. Just because it says “smart” on the box doesn’t mean it plays well with others. When a new device won’t interact with your network, it can mean money down the drain.
Before you buy, check to ensure your devices are compatible with each other. Build your devices around your smart home platform. Review the manufacturer’s specifications thoroughly to avoid compatibility headaches.
5. Security Concerns
Security is paramount in a smart home. There have been horror stories about hacked baby monitors. These stories can get real very fast. You need to pay attention to securing your devices. Rather than getting caught up in plugging them in as fast as possible.
Use strong and unique passwords for all your devices and accounts. Enable two-factor authentication wherever available. Keep your devices and apps updated with the latest security patches.
A few other smart device security tips include:
- Change the default device name on your network. Choose something generic.
- Put smart devices on a separate “guest” network. This keeps them separated from devices with more sensitive data.
- Turn off unnecessary sharing features. These are often enabled by default.
6. App Troubles
Are you running into sporadic problems? Bugs that crop up intermittently?
Sometimes, the problem might lie with the app itself. Check if any app updates are available and install them. Try logging out and logging back in to refresh the connection. If issues persist, uninstall and reinstall the app.
7. Automation Gone Wrong
Smart home automations can be convenient, but sometimes they malfunction. Review your automation rules and ensure they’re set up correctly. Test them individually to identify any faulty triggers or actions.
8. Limited Range
Some smart devices have a limited range. Check the manufacturer’s guide so you know what to expect. Move your devices closer to the hub or router for better communication. Consider using repeaters or extenders if the distance is an issue.
9. Ghost Activity
Ever experienced your smart lights turning on or off randomly? This could be due to factors such as:
- Accidental voice commands
- Faulty sensors
- Scheduled automations you forgot about
- A hacked device
Review your automation settings and disable any you don’t need. Investigate if your devices are picking up unintended voice commands from other sources. Change passwords and watch out for breaches.
10. Feeling Overwhelmed
It’s easy to get overwhelmed when you’re dealing with several smart devices. Don’t hesitate to consult your device manuals and online resources. You can also get help from our IT experts for specific troubleshooting steps. These resources can offer more guidance tailored to your situation.
Need Help Securing Your Smart Home?
A smart home should simplify your life, not complicate it. These simple solutions can help you navigate common issues. It’s also important to get a smart home security assessment to keep your family protected.
Contact us today to schedule a security checkup for your smart home and gain peace of mind.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.
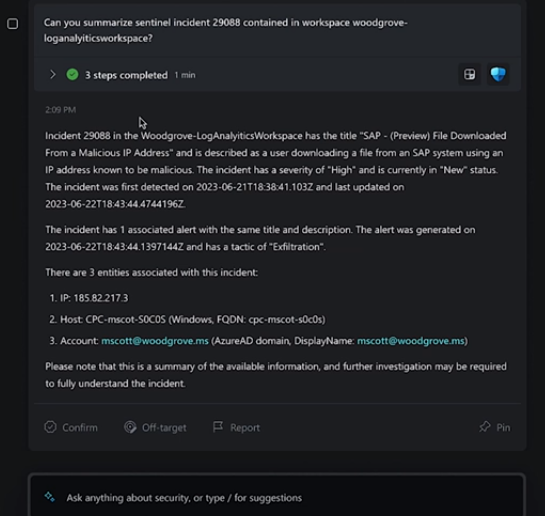
by Blog | Apr 30, 2024 | Microsoft
It can be challenging to keep up with the ever-evolving cyber threat landscape. Companies need to process large amounts of data. As well as respond to incidents quickly and effectively. Managing an organization’s security posture is complex.
That’s where Microsoft Security Copilot comes in. Microsoft Security Copilot is a generative AI-powered security solution. It provides tailored insights that empower your team to defend your network. It works with other Microsoft security products. It also integrates with natural language to generate tailored guidance and insights.
In this article, we will explain what Microsoft Security Copilot is. We’ll explore its benefits and whether it’s the right choice to enhance your digital defenses.
What Is Microsoft Security Copilot?
Microsoft Security Copilot is a cutting-edge cybersecurity tool. It leverages the power of AI and machine learning for threat detection and response. Copilot aims to enhance the efficiency and effectiveness of cybersecurity operations.
Microsoft Security Copilot helps security teams:
- Respond to cyber threats
- Process signals
- Assess risk exposure at machine speed
It works with other Microsoft security products as well. A big benefit is that it integrates with natural language. This means you can ask questions plainly to generate tailored guidance and insights.
Security Copilot can help with end-to-end scenarios such as:
- Incident response
- Threat hunting
- Intelligence gathering
- Posture management
- Executive summaries on security investigations
How Does Microsoft Security Copilot Work?
You can access Microsoft Security Copilot capabilities through a standalone experience. As well as embedded experiences available in other Microsoft security products.
Copilot integrates with several tools, including:
- Microsoft Sentinel
- Microsoft Defender XDR
- Microsoft Intune
- Microsoft Defender Threat Intelligence
- Microsoft Entra
- Microsoft Purview
- Microsoft Defender External Attack Surface Management
- Microsoft Defender for Cloud
You can use natural language prompts with Security Copilot. This makes it easy to ask for information or guidance on various security topics.
For example, you can ask:
- What are the best practices for securing Azure workloads?
- What is the impact of CVE-2024-23905 on my organization?
- Generate a report on the latest attack campaign.
- How do I remediate an incident involving TrickBot malware?
Should You Use Microsoft Security Copilot?
The Pros:
- Advanced Threat Detection
Microsoft Security Copilot employs advanced algorithms. These detect and analyze threats that may go unnoticed by traditional security measures. It has the ability to adapt to new threats in real time. This enhances the security posture for organizations.
- Operational Efficiency
Copilot automates threat analysis. This allows security teams to focus on strategic decision-making. It also reduces the time and effort spent on manual data analysis. The tool streamlines workflows, enabling quicker responses to potential threats.
- Integration with Microsoft Products
Microsoft Security Copilot seamlessly integrates with several Microsoft products. This creates a comprehensive cybersecurity ecosystem. The synergy between these tools enhances threat visibility as well as response capabilities.
- Continuous Learning
The AI and machine learning components of Copilot continuously learn from new data. This improves their ability to identify and mitigate emerging threats over time. This adaptive learning approach ensures that the tool evolves. Which is important to do alongside the ever-changing threat landscape.
- Reduced False Positives
Copilot’s advanced algorithms contribute to a more accurate threat detection process. This minimizes false positives that can overwhelm security teams. The result is a more focused and efficient response to genuine threats.
The Considerations:
- Integration Challenges
Microsoft Security Copilot seamlessly integrates with Microsoft and other security products. But organizations using a diverse range of cybersecurity tools may face integration challenges. Consider the compatibility of Copilot with your existing cybersecurity infrastructure.
- Resource Requirements
The deployment of advanced AI and machine learning technologies may demand extra resources. Companies should check if their existing infrastructure supports the requirements of the tool.
- Training and Familiarization
Successfully leveraging the benefits of Copilot requires training. As well as familiarization with the tool’s functionalities. Ensure that your security team is adequately trained. This will maximize the potential of this cybersecurity solution.
The Bottom Line
Microsoft Security Copilot represents a leap forward in the realm of AI-driven cybersecurity. It has an advanced capacity for real-time threat detection and operational efficiency. As well as extensive integration capabilities. These factors make it a compelling choice. Especially for businesses seeking to fortify their
digital defenses.
Your unique business needs should guide the decision to adopt Microsoft Security Copilot. Consider factors such as existing cybersecurity infrastructure and resource availability. As well as the commitment to ongoing training.
Get Expert Microsoft Product Support Here!
Microsoft is a vast ecosystem of interconnected business tools. Security Copilot is one of the newest to help you secure your online landscape. If you need some help leveraging these tools for your company, let us know. We are experienced Microsoft service providers. Our team can help you make the most of these tools.
Contact us today to schedule a consultation.
—
Featured Image Credit
This Article has been Republished with Permission from The Technology Press.